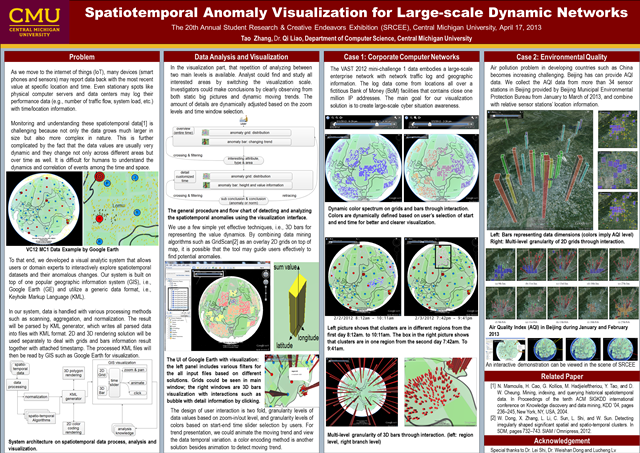
The 20th Annual Student Research & Creative Endeavors Exhibition (SRCEE),Central Michigan University, April 17, 2013
CMU CPS Graduate Research Seminar Talk Spring 2012
CMU and You Day 2011 Research Poster
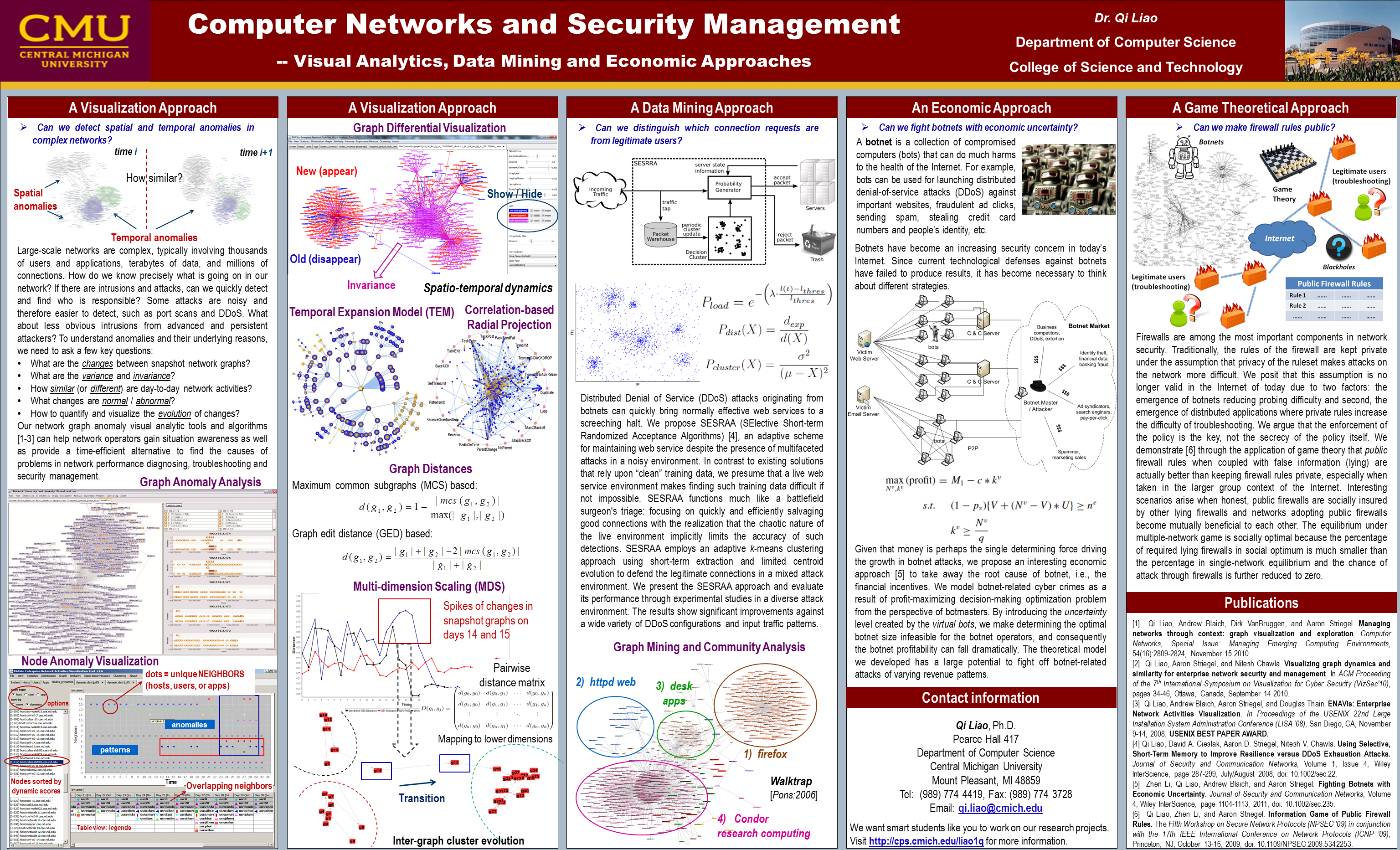
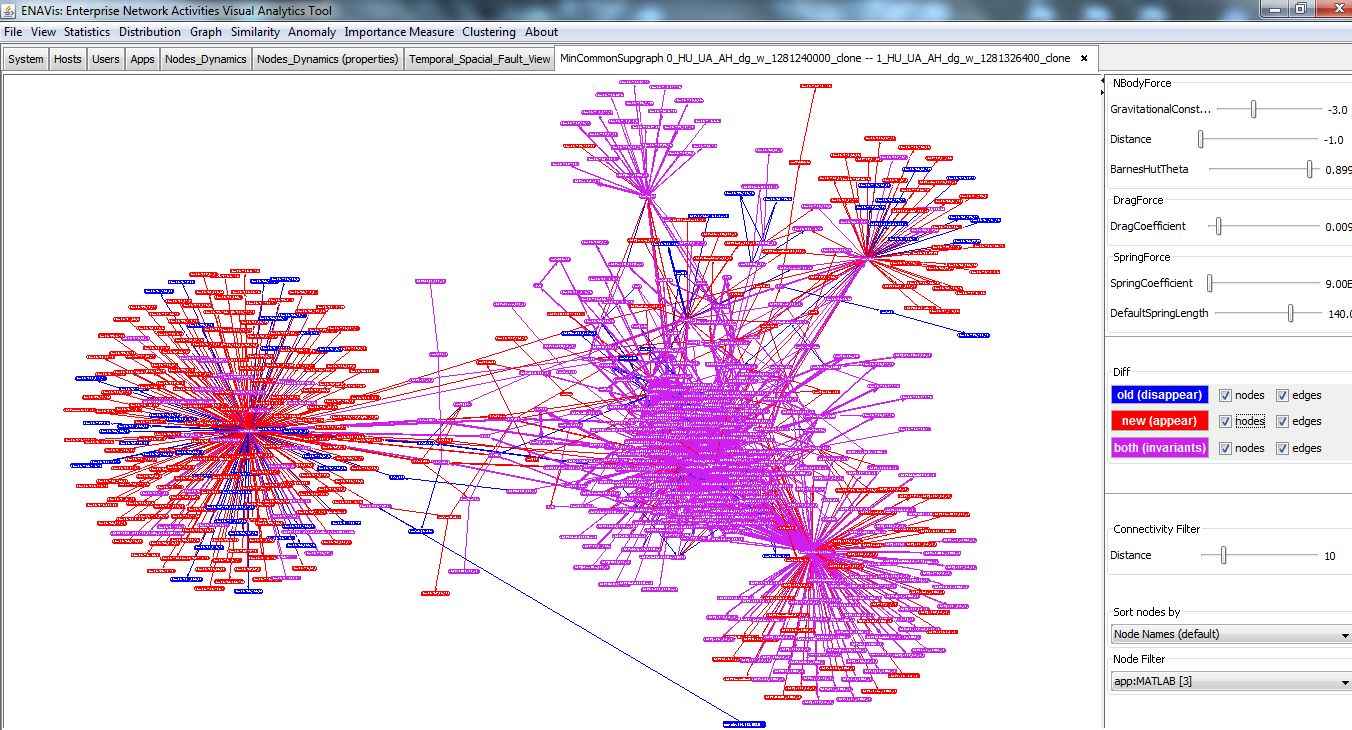
Network Security and Anomaly Visualization
Large-scale enterprise networks typically involve thousands of users and applications, terabytes of data, millions of connections. How do we know precisely what is going on in our network? If there are intrusions and attacks, can we quickly detect and find who is responsible? Some attacks are noisy and easier to detect, such as port scans and DDoS. What about less obvious intrusions from advanced and persistent attackers? A few key questions to ask: • What are the changes happened in networks?
• What are the variance and invariance?
• How similar (or different) from day-to-day network activities?
• What changes are normal / abnormal?
• How to quantify and visualize the evolution of changes? |
Visual Analytics for Science and Technologies
Many of the visualization and analytic methods are not restricted to security management in enterprise networks. Beyond computer and network security, visualization and analytic methods can also be applied to solve various hard problems in other domains. To give a few examples, biological networks such as DNA/RNA, protein-to-protein networks; social networks such as Facebooks/Twitter, emails, phone calls, text messages, etc; Internet of things (IoT). The future of the internet is not just computer-to-computer, but every object or thing. For example, imagine all the mobile devices such as smart phones are now connected to internet, or even home appliances such as TVs and refrigirators are also connected to the internet. Sensor neworks, vehicle-to-vehicle network, you name it. The point is networks are everywhere! |
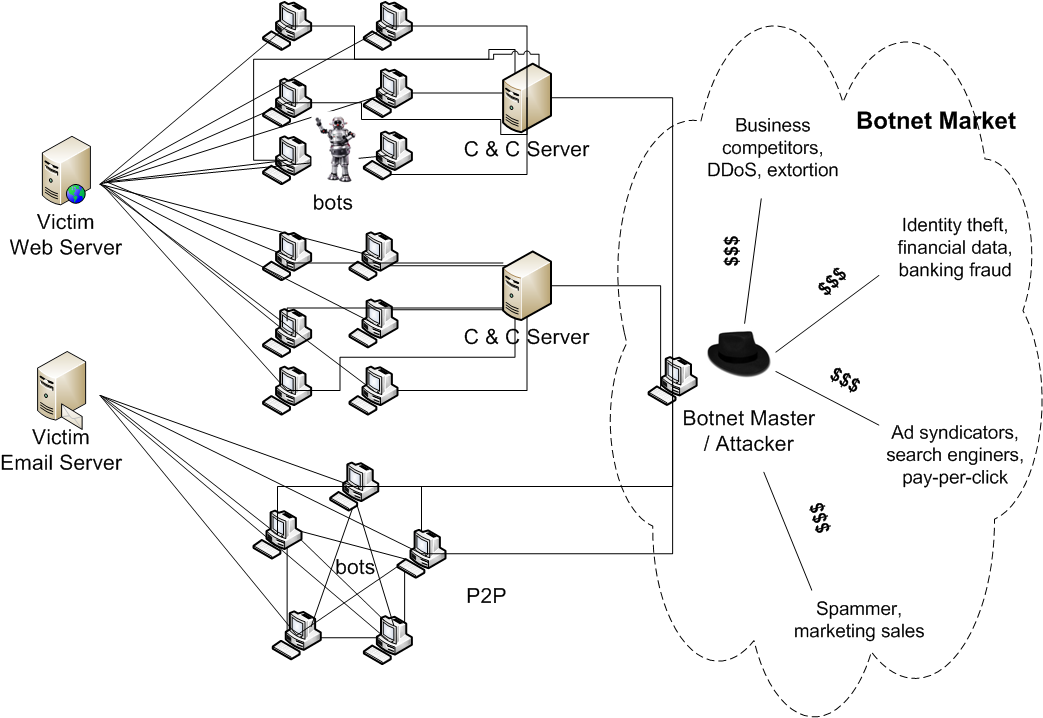
Economics of information security
Do you still remember the hackers from 1970s and 1980s? There were computer elites who broke into systems to proove their programming skills and how smart they are. During the past decades the cybercriminals are not just doing this for fun. They are doing this for profits and it is a million-dollar industry. It is interesting to see that many of nowadays security problems such as Botnet attacks are essentially economic problems. Therefore, removing the root cause, i.e., the financial incentives, seems to be a promising approach. Game theory is another interesting area to explore for understanding and modeling the attacker/defender behaviors. My research group also conducts interdisciplinary research between computer security and economics. |
|
Research and teaching

Read more on the research projects and course offerings.
Current projects
Current classes